15 Cybersecurity Tools for Small and Medium Businesses In 2024

Do you own a business and want to protect it from intruders? Well! There is nothing more effective than cybersecurity in this ever-evolving digital threat landscape. Cybercriminals keep devising new ways to harm your online reputation, but cybersecurity is also not off pace.
Researchers have introduced highly effective cybersecurity tools for business such as antivirus software, DNS, firewalls, EDR, IPS, VPNs, and many more.
All this effort is made to safeguard your developing merchandise from malware attacks, ransomware, phishing attacks, DDoS attacks, and other cyberattacks. Read on to learn more!
Importance of Cybersecurity for Businesses
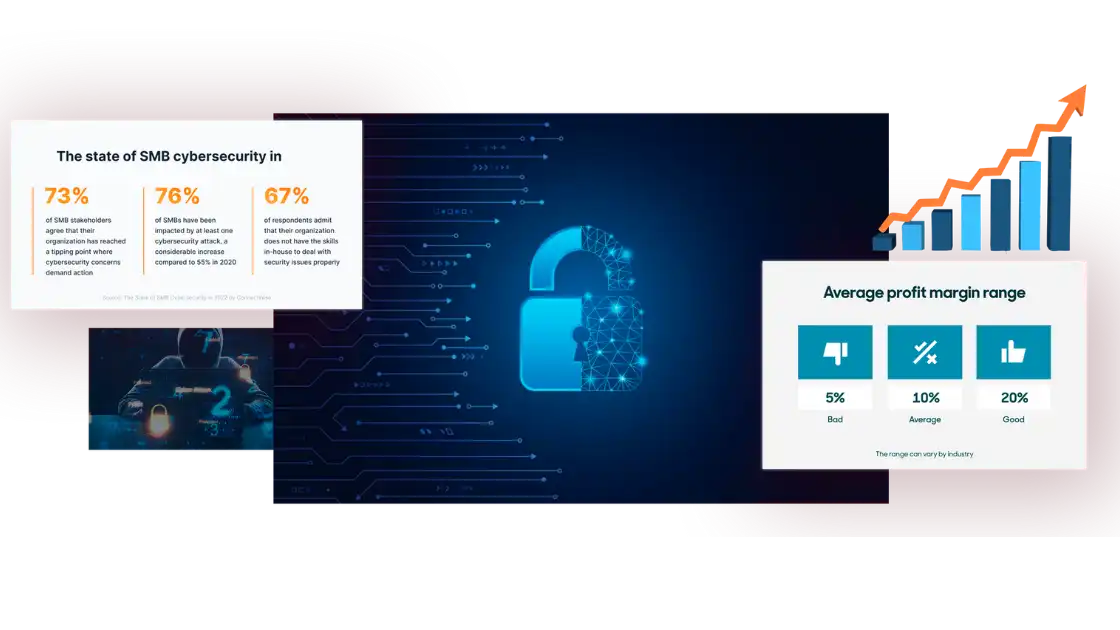
If you have a startup, you must control your expenses to maintain your profit margins and the budget required to expand and improve your business. However, in doing so, entrepreneurs sometimes sacrifice strong security systems by relying on free offers that may not fulfill their business needs. In some cases, the cybersecurity tools utilized by small businesses are the same as those used by individual users.
We have a better alternative. No matter how expanded your business is, you can use the tools required to safeguard your digital assets. All you need is the best small business cybersecurity guide.
Dive deep to explore cybersecurity tools for all types of businesses and some specific SMB cybersecurity tools you can consider to strengthen your defense system against hackers and data breaches. But first, let’s see what are the common cybersecurity threats for businesses.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
- Rated 4.5/5 on Google Play with over 825,000 reviews
- Rated 4.7/5 on Apple App Store from 6,600 users
What are the Common Cybersecurity Threats to Businesses?

Many cybersecurity experts believe that malware is the most common type of cyber attack. It’s basically because malware is a broad class that covers different threat vectors.
Malware is an abbreviation for malicious software that is taken as software made to implement a harmful effect on a device, network, or server. Subcategories like ransomware, phishing attacks, viruses, worms, spyware, trojans, and more. To stay safe in the ever-changing environment, businesses and organizations need to understand them.
- Phishing is an attempt by hackers to acquire information such as usernames and passwords or even bank details through deceptive emails. Here is detailed guide on phishing attacks.
- Ransomware is a type of malicious software that blocks usage or access to a device or system until a ransom is paid to unblock access.
- DDoS attacks are distributed denial-of-service attacks designed to overpower web applications with excessive traffic that interrupt normal service functionality.
Cyberattacks had destructive effects on businesses and organizations both small and large in the past. Do you know about the 2017 WannaCry ransomware attack? It affected thousands of organizations globally.
Similarly, Microsoft was recently hit by a mega phishing scam that influenced over 800 victims across 50 countries. Cybersecurity measures must be put in place to ensure data remains secure from these ever-evolving threats.
Empower Your Business with Cybersecurity Technology

A lot of cybersecurity tools are in use these days for managing and protecting SMBs. Choosing the right type of security software or hardware can equip your business with maximum ROI potential without compromising safety. The secret is to use the technology that helps you get ahead of the attackers’ tactics and varied combos of threats.
The exciting news is it’s not as tricky as you think. The reason is these tools have been made to protect against a wide variety of cyber threats. Whether you have to protect your employees’ emails, your websites, business applications, or endpoints, there are different types of cybersecurity tools to choose from.
Network Security Tools
You might have heard of software firewalls. They are indispensable in guaranteeing network security. Firewalls work best along with other security technologies such as:
- Network traffic analysis tools
- Intrusion detection and prevention systems
- Vulnerability scanners
These additional tools add an extra layer of defense against malware attacks. We suggest you install firewalls to ensure that only authorized traffic enters your safe network after getting through the firewall.
Application Security Tools
Cybersecurity is a considerable part of any online business, especially due to the increased dependence on digital services and frameworks. However, businesses can ensure the security of their web environments by using the right tools. Here we have mentioned two of them.
- Static Application Security Testing (SAST) Tools: These cybersecurity tools enhance security by constantly monitoring the risks of malicious attacks or code segments during all parts of the software development life cycle.
- Dynamic Application Security Testing (DAST) Tools: These tools work together with application firewalls (WAFs) to protect against runtime errors.
Endpoint Security Tools
Some important cybersecurity tools like firewalls, anti-malware, and antivirus software, plus mobile device management (MDM) tools, patch management, and end-point encryption tools, help ensure the security of your business.
Endpoint encryption is effective in protecting important information stored on an employee’s laptop while MDM can be used to remotely manage devices owned by a company.
Data Security Tools
Firewalls and other cybersecurity tools like data loss prevention (DLP) software, access control and identity management software, security information and event management (SIEM) tools, and backup and recovery software are crucial for keeping your data and network secure.
Firewall systems provide additional security by blocking malicious traffic from outside the network while DLP software monitors the system for any unauthorized activity.
Cloud Security Tools
As our reliance on cloud technology grows, firewall protection and cybersecurity are becoming more and more crucial. Fortunately, there are tools out there that can help secure our cloud-based systems, including:
- Cloud access security brokers (CASBs)
- Identity and access management (IAM) tools
- Encryption and tokenization software
- Cloud workload protection platforms (CWPPs)
- Cloud security posture management (CSPM) tools.
Threat Intelligence and Incidence Response Tools
Cybersecurity is an ever-evolving challenge for organizations of all sizes. To stay ahead of potential threats, it’s essential to leverage a range of meaningful tools and policies.
Security information and event management (SIEM) tools help companies to detect, investigate, and respond proactively to cyber threats. They can be combined with threat intelligence platforms (TIPs) to collect, monitor, and analyze digital risk data in real-time.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
- Rated 4.5/5 on Google Play with over 825,000 reviews
- Rated 4.7/5 on Apple App Store from 6,600 users
15 Important Cybersecurity Tools for Businesses

Despite the ever-evolving digital landscape, there are 15 important cybersecurity tools and services that will always help secure your IT environment.
Antivirus Software
No doubt antivirus software has lately been very effective in fighting against computer viruses, but modern antivirus solutions protect against a lot more threats. A powerful antivirus program can detect unknown malware attacks while looking for the presence of known threats.
Antivirus software utilizes the previous descriptions of attacks that have influenced users. It examines your system to know if such malicious programs are present on your computer, notifies you about unfavorable elements, and removes them. As a result, with the right antivirus software, you can guard yourself against many threatening cyberattacks.
Domain Name System (DNS) Protection
Domain Name System (DNS) protection provides you with an additional layer of defense by stopping employees from opening dangerous websites. Such systems also infiltrate your network to remove content you don’t want to access and also the content you don’t want your users to see.
For instance, if a worker commonly accesses a website known for threats in their private time, they may tend to open that same website during their working hours. However, your DNS protection system inhibits their access to these websites when they are working on your network.
Endpoint Detection and Responses (EDR)
Endpoint detection and response (EDR) solutions have made it convenient to detect devices connected to your network and work against threats that the system identifies.
For instance, if someone connects to your network with malicious intentions, your endpoint detection and response system can give a detailed description of the device connected. It also provides its activity data while it’s joined to your network.
An EDR tool not only prevents unwanted users and devices from joining your network, but it’s also efficient enough to gather forensic information related to a data breach. The logs made by the system can be analyzed to know who connected and whether or not they were accountable for the data breach.
Next-generation firewalls (NGFW)
Next-generation firewalls (NGFW) ensure complete protection against a lot of threats. They also make it easier for outsiders to connect to your network securely. They inspect data packets as they are transmitted within your network. If a known problem is seen, your NGFW can automatically remove the vulnerable data packet.
Moreover, the right next-generation firewall takes advantage of machine learning that can detect malicious attacks. Consequently, zero-day attacks can also be terminated because the type of malicious code can be identified even without notifying the system of its presence beforehand. An NGFW can also help to set up a virtual private network (VPN).
Intrusion Detection and Prevention (IDS/IPS)
Intrusion detection and response systems examine the content of data packets as they try to enter your network. This feature differentiates it from a typical firewall, which examines data inside the headers of data packets.
By using an intrusion detection and prevention system, you can block many different threats, especially if your system is based on a comprehensive threat intelligence platform to detect malicious code.
Email Gateway Security
By using email gateway security, you can prevent unwanted emails from accessing the accounts of your users. This involves both annoying emails like direct threats and spam, such as emails containing malware.
For example, suppose you have a small office connected to your main center of operations via a software-defined wide-area network (SD-WAN), and you need to ensure the safety of all users, regardless of their location.
With an email gateway security system, you simply identify the unusual messages as dangerous or unwanted and your users will not receive these messages while using your small business’s email service. This keeps your network threat-free and also ensures that the email storage space is not stuffed with spam.
VPN or Authentication Services
By using an authentication service, you can prevent unwanted users and hackers from entering your network. You can do this by defining a privileged access management (PAM) system that allows users to authenticate their names before connecting to your system.
And the best thing? A powerful VPN. Using a VPN is a straightforward way of preventing highly unsafe users from accessing your digital assets. A VPN not only requires all users to give login credentials but also encrypts all the data exchanged between them and your system.
In such a way, their devices, as well as your network, are guarded against outer threats. We can purchase a reliable and robust VPN from VPN.com at a reasonable price.
Data Backups
Cloud storage is now the best practice for backing up important business data. A brief research search shows that over 50 percent of organizations depend only on cloud-based backup storage.
When compared with on-site data storage techniques, cloud storage offers benefits such as protection against physical and natural disasters.
Logging and Log Monitoring
Logging the events that affect your network and checking activity can help prevent threats and understand how they entered your system and caused a breach. The logs give detailed information such as time-stamped records of activity, which causes attacks on the devices or users that can easily be detected as a cause.
Web Application Firewalls
Web application firewalls (WAFs) protect your web-based applications from hackers who may try to penetrate them to steal information or misuse a vulnerability in a web app. All traffic transmitted over your web service is filtered, and if a threat is seen, the data related to it can be removed automatically.
Many small and medium businesses use WAFs to protect their precious websites from hackers, distributed denial of service(DDoS) attacks, and other insider threats.
SD-WAN
Software-defined wide-area networks (SD-WAN) enable you to control the management of traffic with minimum detail. Using SD-WAN, you can improve how your digital assets are used to ensure adequate support and cyber safety simultaneously.
Instead of your traffic passing through your network randomly, you can change the route of one kind of data while sending other kinds somewhere else. It gives users a more stable, safer experience. With SD-WAN, you can also reduce the cost of bandwidth as you can make the most of your current service.
Cloud-based Security
Cloud-based security is a vast domain that involves the technologies and policies used to protect cloud-based resources from cyberattacks. These kinds of solutions protect cloud assets, such as your:
- Data
- Services
- Applications
- Cloud infrastructure
Enterprise Password Management or Privileged Access Management
With enterprise password management and PAM, you get control over the activities and identities of all devices and users that interact with your network. Only those given access details are allowed to interfere with your network, and if their activity becomes harmful, you can cancel their access.
Moreover, if a user is no longer allowed to connect, for instance, when they have been fired from your company, you can easily ensure they can no longer access your system.
Vulnerability and Threat Management
Vulnerability and threat management mean limiting your business’s exposure to threats and ensuring that endpoints are secured enough that your company stays resilient in the event of a breach. This involves a systematic approach to technologies, such as endpoint protection tools, people, and policies.
Vulnerability assessment also needs a system for reporting issues. It enables you to mark weaknesses and prevent serious breaches along the way.
Threat Detection
Threat detection means monitoring all the resources connected to your network, as well as the network itself, for any unusual activity, users, and applications. A threat detection system makes use of the data generated by different events on your network to detect cyber safety problems.
It can also involve a sandbox which contains threats in a separate environment. It helps keep threats away from sensitive parts of your network. As the threat is within this controlled environment, its activity is carefully monitored which allows admins to study and learn from it.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
- Rated 4.5/5 on Google Play with over 825,000 reviews
- Rated 4.7/5 on Apple App Store from 6,600 users
Frequently Asked Questions
What Are the Tools Required for Cybersecurity?
The important tools required for cybersecurity are virtual private network (VPN), antivirus software, endpoint detection and response (EDR), Domain Name System (DNS) protection, next-generation firewalls (NGFW), logging and log monitoring, email gateway security, intrusion detection and prevention, web application firewalls (WAFs), endpoint protection, authentication services, cloud-based security, privileged access management (PAM), software-defined wide-area networks (SD-WAN), enterprise password management, threat detection, and vulnerability and threat management.
How Do I Secure My Small Business Network?
The only way to secure your small business network is by selecting security tools based on your digital assets, network structure, and stability of cloud and on-site systems.
What are the Cybersecurity Tools Used in Storing Business Tools?
Some security tools you can use to store business tools may include next-generation firewalls and web application firewalls. These cybersecurity tools protect your business assets from nasty websites, users, and software.
The Bottom Line
To put all this data in a nutshell, we can say cybersecurity tools are important for businesses to protect their digital assets and prevent data breaches. Tools like antivirus software, firewalls, EDR, and VPNs provide strict security against cyber threats.
A VPN is an essential tool that encrypts data and hides online activities to ensure complete privacy and security of your business network. It protects your system from hackers, malware, and unauthorized access.
To improve your business’s cybersecurity, invest in a powerful VPN from VPN.com today. Their reliable VPNs will keep your data and network secure and allow you to operate without worrying about cyber attacks.
Customer Reviews for NordVPN: In-Depth Review, Tests, and Stats
![15 Cybersecurity Tools for Small and Medium Businesses In [year]](https://cdn.vpn.com/wp-content/themes/VPN/images/trustpilot/trustpilot_5_star.png)
Connection issues with MLB.TV
May, 2 2023
![15 Cybersecurity Tools for Small and Medium Businesses In [year]](https://cdn.vpn.com/wp-content/themes/VPN/images/trustpilot/trustpilot_5_star.png)
Prompt customer service
May, 6 2023
![15 Cybersecurity Tools for Small and Medium Businesses In [year]](https://cdn.vpn.com/wp-content/themes/VPN/images/trustpilot/trustpilot_5_star.png)
I would highly recommend
December, 15 2023

![15 Cybersecurity Tools for Small and Medium Businesses In [year]](https://cdn.vpn.com/wp-content/themes/VPN/images/icons/payment-methods/mastercard.png)
![15 Cybersecurity Tools for Small and Medium Businesses In [year]](https://cdn.vpn.com/wp-content/themes/VPN/images/icons/payment-methods/american_express.png)
![15 Cybersecurity Tools for Small and Medium Businesses In [year]](https://cdn.vpn.com/wp-content/themes/VPN/images/icons/payment-methods/discover.png)