Data Privacy, Laws And Ways To Protect Your Personal Information

We live in a digital world. Where everything now shifted on the internet. Even if you want to shop something for yourself you have to go online. And as everything is going online, some folks are also anxious about their privacy. Are they safe? Is everything they do online is kept to them only? They are so concerned that, now, to even do a simple thing like to talk to someone you have to ask their permission first.
You should be caring about your peacefulness as well. As everything is going online, criminals are also present there. Yes, there are many threats to your online privacy. Your data can be used against you and you may not even have a clue. And it might be possible that you can’t save it from happening.
But enough with the scary stuff. We are here to give you some good news. Due to some of criminal activities there have been some developments in data privacy. Some laws are created just for you to protect your private information. These laws are designed for your rights of privacy. And we are always here for you. We will properly guide you on different ways to protect your personal information from threats that are lurking around.
What is Data Privacy?
Data privacy or the privacy of your information. It means how your personal data will be controlled, processed and preserved. Your personal data or information can be anything that is related to you, from your name to your dog’s name, from where you live to where you bury your loved ones. We think that such information should be kept to you and you only.
In terms of online, your personal data could be what you do online, who you contact with and what you like to shop for yourself or for anyone. Don’t you think that such things should be only kept to you only? No one wants their data to be used or even get in the wrong hands. You can trust anyone now can you? The main goal of data privacy is to make sure that your data is handled by the right hands. Because you have a right to keep your data protected.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
- Rated 4.5/5 on Google Play with over 825,000 reviews
- Rated 4.7/5 on Apple App Store from 6,600 users
Threats to Your Privacy

You may be already aware of some threats to your online privacy. But there are more ways to hurt you than you know. Cybercriminals are very sneaky in these things. We are here to tell you about such threats like:
Social Engineering
Social Engineering is a collective of multiple methods that a cybercriminal will apply to you or someone else to get them to reveal their personal data. In social engineering there are multiple techniques to deceive one. Hackers might send you a text to help some poor child or even create a fake scenario for you as bait. Or even offer some smart deal about something that might seem attractive but actually it isn’t.
Malware
Malware is a software which is made by cybercriminals. Its main purpose is to hurt you in some kind of way. And yes it can hurt you in many ways. What they do is send you an email or a text. The email might not look like a fake but once you click on it then it’s game over for you. The email or a link that the email might have by clicking on it will trigger a series of codes that will execute without you knowing. It will download software that contains some kind of virus.
That software will do pretty much anything. It can steal your login and passwords. It can fill your device with encryption keys and to decrypt it a hacker might ask for money or something valuable to you. It can also access your camera or mic to monitor your activities. If you want to know more about Malware and its types you must visit this guide.
Spear Phishing
You might have heard of Phishing. In this, hackers manipulate anyone to reveal their personal information. But in spear phishing the hacker becomes even more sneaky with his attacks. Hackers will specifically target you with the information they have on you. Then the hacker will convince you to tell him more of your personal details. You can get in-depth details about this highly targeted form of phishing by visiting this guide.
Network Attacks
Using public WiFi is not safe at all. Better not use it. Because public WiFi is not that securely encrypted. So anyone can hack it pretty easily. Hackers are also connected to the public WiFi. Which means they can see what you do online. If you are communicating with someone while connected to a public WiFi. Then who knows who else might be listening to your conversation.
Internet of Things (IoT)
There are many devices that use the internet. You might even have an old phone or a laptop that might be in use. But old devices do not have any new kind of security features. Which makes them vulnerable to many online threats. These devices might even contain important data of yours. If it gets in the wrong hands, who knows what it can be used for.
Social Media Exploitation
The social media platforms you use. Are they safe? Not at all. Even they collect your data for multiple purposes. The reason could be target advertising or manipulation. Hackers are also present on these platforms waiting for you to give information by yourself or to upload something.
Deepfakes
There are many AI websites or bots that can create any image, any voice or even text. Cybercriminals use these AI tools to hurt your reputation in front of your loved ones or friends.
What Data Can Be Targeted?

Cybercriminals usually go for your personal things first. For example your name, contact number, social security number and address. These are very common to steal. Even more personal to that is your online activities and your financial information. Like how they can steal that or how to manipulate you to give it yourself. The more important question related to your private information is, what do they do with it? And how can it be used to hurt you?
Identity Theft
Your identity should be personal to you. As no one else can be you. But cybercriminals can impersonate you by using your personal information and doing many evil things. Like misguiding your friends or family, posting fake things about you on social media or even making fake medical records in your name. If you are curious about how identity theft does work, you can check out this guide.
Doxxing
This is an act in which cybercriminals spread your personal information to the world, which can lead to many harmful things. Like embarrassment, privacy invasion or you can even get threats. It’s a matter of your reputation.
Sell It on the Dark Web
Your private information is not only vital to you but also essential to many cybercriminals. There is a special marketplace just for private data of many people on the dark web. Information about important personalities is more valuable. The dark web is a place you don’t want your private data to be.
Financial Exploitation
Cybercriminals can use your credit card information for their own benefit. They can even make purchases or transfers your hard earned money which are not authorized by you. They can even apply for loans in your name and leave you with a huge debt.
Extortion and Blackmail
Can your data be used against you? Yes it can. Many cybercriminals steal your data then they blackmail or threaten you to give them something as a payment. And if you don’t agree with this then they blackmail you so that they will reveal this sensitive information to the public.
Personal Exploitation
Your personal data can be used to stalk you or your loved ones. Sometimes it can even lead to harassment. Many cybercriminals commit crimes using your name. Which then also hurts your personality and reputation.
Data Privacy Laws
Laws are the regulations and rules but for data privacy it is the rules that are made for keeping your data safe and sound just for you. These laws are made so that we know how your data is collected, stored, processed and then shared with others. But don’t you worry these laws are not here just for that, they also help you so that you can keep your data safe from any one who means you harm.
Importance
With the rise of threats on the internet, data privacy laws are here to help us. They do more than just protect your private information. They protect you from any cyber criminality, prevent you from theft of your identity and give you control over your personal information.
Not only that, they also create guidelines and provide a special framework for you to follow. They give rights and control to you so that you can change or even delete your personal data. Also this information of yours can be seen or accessed by only those who you authorize. And don’t forget it will also inform you about any data breaches that can or will happen. Let us tell you about some main data privacy laws that are used and implemented around the globe.
General Data Protection Regulation (GDPR)
- Region: European Union (EU)
- Effective Date: May 25, 2018
Key Provisions
- Consent: Requires exact consent from people for processing.of data
- Data Subject Rights: Grants rights to erase, correct, access and restrict the processing of private data.
- Data Breach Notification: Company must report data breaches in 72 hours.
- Fine: About 20,000,000 Euro or 4% of annual global revenue whatever is more.
California Consumer Privacy Act (CCPA)
- Region: California, USA
- Effective Date: January 1, 2020
Key Provisions
- Right to Know: Customers can request data about the use, collection and sharing of their private information.
- Right to Delete: Customers can demand to delete their private informaton.
- Fine: Fines for violations range from $2,500 to $7,500 per incident.
Personal Data Protection Act (PDPA) – Singapore
- Region: Singapore
- Effective Date: July 2, 2014
Key Provisions
- Consent: Requires companies to obtain agreement before using, collecting or disclosing private information.
- Access and Correction: Grants individuals the right to obtain and alter their private information.
- Data Security: Organizations must protect personal data with reasonable security arrangements.
- Fine: Fines up to SGD 1 million.
Brazilian General Data Protection Law (LGPD)
- Region: Brazil
- Effective Date: August 15, 2020
Key Provisions
- Consent: Need clear and exact agreement for the processing of data.
- Data Subject Rights: Provides rights to edit, access, delete and port personal information.
- Data Protection Officer: Companies must appoint an information protection officer.
- Fine: About 2% of a company’s turnover in Brazil capped at 50 million reais per disobeying.
Personal Information Protection and Electronic Documents Act (PIPEDA) – Canada
- Region: Canada
- Effective Date: April 13, 2000 (with amendments over time)
Key Provisions
- Consent: Requires organizations to obtain meaningful consent for data collection and use.
- Access and Correction: Grants individuals the right to obtain and alter their private information.
- Data Security: Organizations must protect personal data with appropriate safeguards.
- Fine: For non-compliance is decided by the Department of the Privacy Commissioner.
New State Data Privacy Laws in the United States
- States: Various, including New Jersey, New Hampshire, Montana, Florida, Texas and Oregon
- Effective Dates: Various dates in 2024 and 2025
Key Provisions
- Consent: Similar requirements for obtaining consent before data processing.
- Data Subject Rights: Rights to edit, obtain, delete and opt-out of processing of information.
- Data Security: Requirements for protecting personal data and conducting data protection assessments.
- Fine: Vary by state including fines and enforcement actions by state authorities.
Ways to Protect Your Personal Information
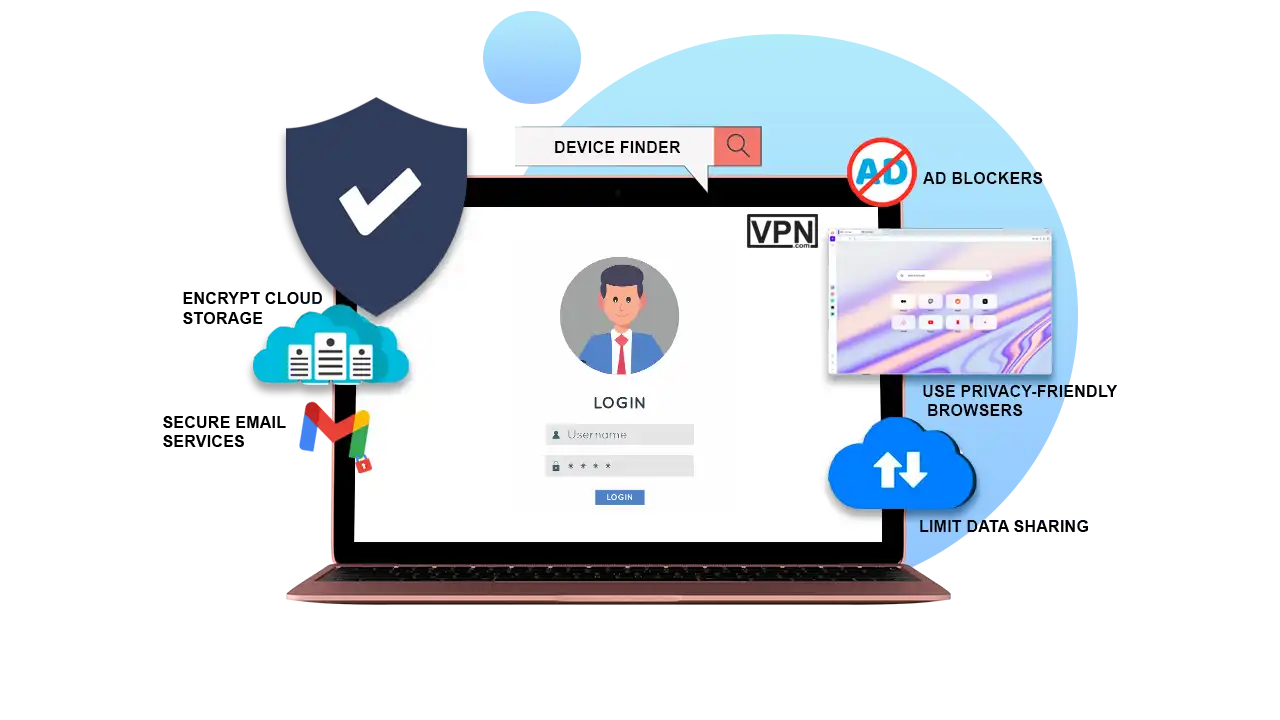
Now don’t you worry. As there are many threats to your online privacy, there are also many ways to protect your personal information as well. We are here for you. We will tell you how you can protect your private information from those who wish you harm. There are some good ways to protect your personal information like:
Use Privacy-Friendly Browsers
Consider using browsers that mainly focus on privacy. By this method it will be very difficult for the attacker to see your activities. Your browser should block any tracker or ads by default. It should also route your internet traffic through many different points and also encrypt it. So that it would be impossible to trace it back to you.
Limit Data Sharing
Telling everyone about yourself is not a smart move. You should also keep in mind to limit what you show on the internet. It won’t hurt you but instead you will benefit from it. The less you tell about yourself the less chances of data leak is there. Especially don’t share sensitive information like your name, your address and your contact information.
Encrypt Cloud Storage
As cloud storage is taking over the internet. If you are using cloud storage it is critical to ensure that it is fully encrypted. Even if it is already encrypted, just for safe keeping your data add another layer of encryption.
Use Device Finder
In case your device gets stolen. You should always keep a device finder app in all of your devices. It will aid you to erase any sensitive data so that it does not get in the wrong hands which will also help to protect your private information.
Review Apps You Use
Always keep a close eye on the applications you use a lot. Many apps ask for the access to your device’s camera, mic and even access to your media. Do not always trust them with these permissions. And also review their policies as many people don’t show any interest in them. Your mic and camera remain on even if there is no use of it and it keeps collecting your data while you are on the app. You should be aware of how they collect your data and how it is used.
Ad Blockers
Add an ad blocked to your browser. It helps so much with the tracking and unwanted ads that keep popping up when you go surfing.
Privacy-Focused Messaging Apps
There are many applications that provide end-to-end encryption and many other features to their users. Use them for your daily conversations. Because they are privacy focused so it is very hard for the hacker to interfere with your conversations.
Use Secure Email Services
For your work related emails, you should consider using a secure email provider. So that you can protect your private information from the common threats. You can get more ways to send emails anonymously by visiting our helpful guide.
Make Your Passwords Impenetrable
You think your passwords are unable to crack? Think again. Majority of the people use very guessable passwords such as “passwords,” “12345678” or their own name and contact number. Not a smart move if you ask us. Always use robust passwords with the help of password generators or password managers. They can create passwords which are very impossible to hack.
Your smartphones are also getting advanced in security. Use biometric authentication. Like fingerprints and facial recognition. Also use long passwords or pin codes. This way you can protect your private information.
App Locks
You can also use another safety feature that smartphones offer. You should use app locks along with your screen lock and pin codes. These so called app locks helps to add another safety layer so that it will be even more hard to gain access to your personal information. And that way you can safely protect your private information.
Regularly Clear Your Browsing Data
It is also a good way to protect your private information from threats. Everyone should know about their own browsing data. If you clear your browsing history then no one else will be able to see it even your own ISP.
If you keep checking your browsing history, then it will help to know if there are any suspicious activities. If you are not the one visiting certain websites then you will know that there is a leak.
Disable Third-Party Cookies
New browsers have this new feature in which you can turn off any third party cookies. This prevents any kind of tracking of your online activities. It is another method to protect your private information.
Enable Do Not Track Requests
Whenever you visit a site they might ask you to allow cookies when then track your activities. Make sure that you don’t allow them to track and also enable “Do Not Track” feature that you might find in your web browser settings. It also prevents any tracking that might already be in place. And don’t forget to disallow any unnecessary permissions on your mobile devices. They also track your activities. It is a way to protect your private information.
Isolate Online Activities
If you want to protect your private information then you don’t want anyone to know about you personal activities. One of the ways to protect your personal information is to use a different browser and make a new account for it. So that every thing you want to keep personal to yourself is separated from your daily activities. Tracking of the websites will also be in a limit this way.
Secure Your IoT Devices
Your old devices that you no longer use. They have very weak security. Change their passwords and review their permissions. They might be a threat to your personal information.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
- Rated 4.5/5 on Google Play with over 825,000 reviews
- Rated 4.7/5 on Apple App Store from 6,600 users
How Can VPNs Help?

VPNs helps more then you know. They increase the security and the privacy of your internet connection. It will encrypt your traffic and then create a tunnel so that all of your internet traffic goes throught it. They also hide your IP address and give you a IP address of the VPN server which is in a remote location.
As it increases your privacy this also helps in the hiding your online activities and stop any king of tracking. So that no hacker or your ISP can see what you are doing online in your private time. It can also help you to access any restricted content and protect from ISP throttling. But despite all of that it assists in boosting security for your internet using devices. Other than that it can stop cybercriminals from interfering with your conversations even if you are connected with a public WiFi.
Our Top Choice
NordVPN gives exactly what you need to protect your personal information. As it recently have some new speed enhancements so that you don’t have any kind of delay while surfing on the internet. With their new and advance security feature it not only will block ads but it will also scans for any malware that is installed in your device.
NordVPN also supports multiple devices at the same time so that their users can keep all of their devices safe from threats. It can prevent any kind of network attack any let you know if you get any scam emails. You can get NordVPN from vpn.com which will also benefit you and will also provide you with a discount on their subscription.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
- Rated 4.5/5 on Google Play with over 825,000 reviews
- Rated 4.7/5 on Apple App Store from 6,600 users
Frequently Asked Questions
What are the laws protecting data privacy?
Key data privacy laws include the GDPR in the EU, the CCPA in California, USA, the PDPA in Singapore, the LGPD in Brazil and the PIPEDA in Canada. These laws establish guidelines for processing of information, grant people rights over their data and impose fines for non-compliance.
How do you protect your private information?
Personal information can be protected by using strong, unique passwords and enabling multi-factor authentication, limiting data sharing on social media and online platforms, regularly updating software and devices, and using privacy-focused browsers and VPNs to encrypt internet traffic and mask IP addresses.
What are 8 ways you can protect personal data?
There are the following ways to protect your personal information use privacy-friendly browsers like Brave or Tor, enable multi-factor authentication, use strong and creative passwords, limit data sharing on social media and other online platforms, encrypt cloud storage and sensitive files, regularly clear browsing data and disable third-party cookies, use ad blockers to prevent tracking, use secure email services and privacy-focused messaging apps.
Which is an effective way to protect personal information?
Using a VPN is an effective way to protect personal information. VPNs encrypt your internet traffic, hide your IP address and protect your online activities from being tracked by ISPs, hackers and other entities.
What are the threats to your personal information?
Threats to personal information include social engineering, malware, phishing and spear phishing attacks, network attacks (especially on public Wi-Fi), IoT vulnerabilities, social media exploitation and deepfakes.
How is your data targeted?
Cybercriminals target data through methods such as phishing, malware, social engineering, and exploiting vulnerabilities in networks and devices. They may use stolen data for identity theft, financial fraud, extortion or selling it on the dark web.
How do VPNs help with your online privacy?
VPNs help protect online privacy by encrypting your internet traffic, masking your IP address, and creating a secure tunnel for your data to travel through. This prevents hackers, ISPs and other entities from monitoring your online activities. VPNs also allow access to restricted content and protect against cyber threats even on public Wi-Fi networks.
The Bottom Line
In our digital world where so much of our personal lives and activities are carry out online in order to protect your private information has never been more important. From everyday internet browsing to online shopping, banking and even communicating with our friends. Every action we take on the internet can expose our personal information to many threats.
But the good news is that growth in data privacy laws and the development of powerful security tools like VPNs offer rare protection against these threats. Understanding the various ways in which our data can be compromised. From phishing attacks and malware to social engineering and network vulnerabilities. VPNs empowers us to take proactive measures.
By choosing robust passwords, using secure browsing habits, using encryption and staying informed about the latest security features we can keep our personal information safe. With tools like NordVPN which offer enhanced privacy and security features we can go around the digital world with greater confidence and peace of mind.
Remember to stay alert, and the best ways to protect your personal information for online security not only protects your personal data but also contributes to a safer internet for everyone. Happy browsing and stay safe online.
Customer Reviews for NordVPN: In-Depth Review, Tests, and Stats

Connection issues with MLB.TV
May, 2 2023

Prompt customer service
May, 6 2023

I would highly recommend
December, 15 2023



