How Does Identity Theft Work?

We all know what identity theft means. It is getting your personal information swiped and then used without permission. Did you know that the numbers for identity theft have shot up big time lately? According to the National Council on Identity Theft Protection, they are going from 3.43 million in 2019 to a whopping 5.74 million in 2021. So, there are different types of identity thefts and each one can mess with you in its own way.
There is no sure way to protect yourself completely from identity theft. But if you take some time to understand that your information can be at risk and what sneaky people can do with you, you will know why it is crucial to keep your data safe. You would now understand why it is essential to take quick action when someone does manage to take it. So, let’s see what dangers identity theft poses to us.
What Is Identity Theft?
We think that before knowing about the dangers of identity theft, we should understand what it is. Identity theft occurs when someone uses your personal information, like your Social Security number, without your permission to commit fraud or other crimes.
These hackers might try to empty your bank and investment accounts, open new credit lines, set up utility services, grab your tax refund, use your insurance details for medical treatments, or even hand out your name and address to the police when things go wrong. Scary, isn’t it?
While data breaches happen often, your information might already be out there; who knows? Given this new reality, we should stop these scammers and hackers from exploiting our details and wrecking our financial world. You should understand why your data privacy is very important.
Do you know that your data can be the reason that companies might discriminate against you based on race, gender, or other factors? Data Privacy is the only way that you can prevent identity thefts in the future. However, there are various other measures, too, like getting a reliable VPN.
They are the masters of anonymity. But don’t forget to get the right one if you are unsure about how to choose the right one. Then, you can choose NordVPN. It is the customer’s best recommendation nowadays.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
GUARANTEE
What Are Types Of Identity Thefts?

You might understand identity theft better by its types. So, the common types include Financial Identity Theft, Tax-Related Identity Theft, Medical Identity Theft, Criminal Identity Theft, Child Identity Theft, Senior Identity Theft, Identity Cloning for Concealment, and Synthetic Identity Theft.
True-Name Identity Theft
This usually occurs when the thief is using Personal Identifiable Information (PII) to open a new account; PII is any information that can be used to uniquely identify, contact, or locate a person. It could involve opening a new credit card, getting cell phone service, or establishing a fresh checking account to grab someone’s blank checks. You really need to be careful of these people.
Account-Takeover Identity Theft
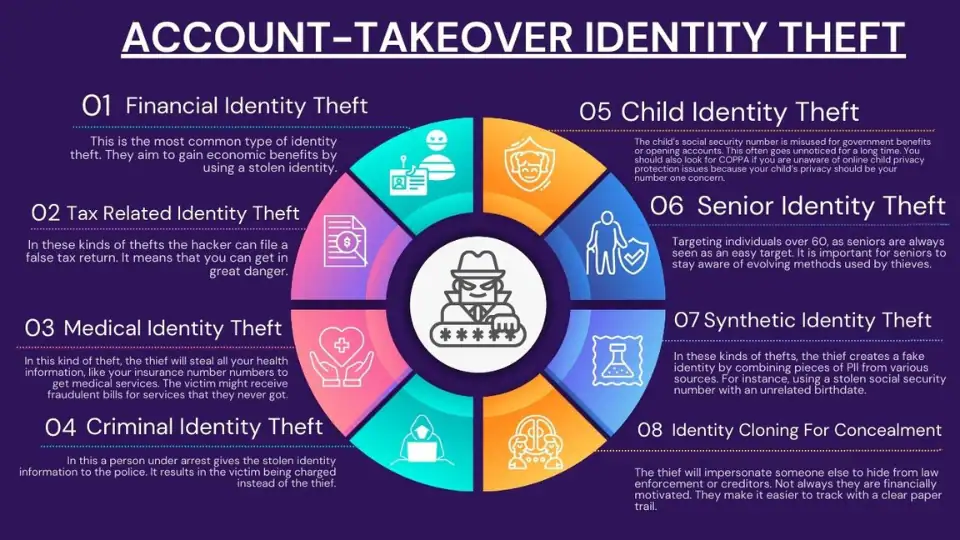
The hacker here will try to use PII to access your existing accounts. Usually, they will change the mailing address on an account and rack up bills before the victim even realizes something is wrong.
The internet has made it simpler for identity thieves to exploit stolen information, especially with online transactions that lack personal interaction. Here are some of the examples of Identity Theft:
- Financial Identity Theft: This is the most common type of identity theft. They aim to gain economic benefits by using a stolen identity.
- Tax Related Identity Theft: In these kinds of thefts the hacker can file a false tax return. It means that you can get in great danger.
- Medical Identity Theft: In this kind of theft, the thief will steal all your health information, like your insurance number numbers to get medical services. The victim might receive fraudulent bills for services that they never got.
- Criminal Identity Theft: In this a person under arrest gives the stolen identity information to the police. It results in the victim being charged instead of the thief.
- Child Identity Theft: The child’s social security number is misused for government benefits or opening accounts. This often goes unnoticed for a long time. You should also look for COPPA if you are unaware of online child privacy protection issues because your child’s privacy should be your number one concern. You shouldn’t give them more information than they should have because that is when they can fall victim to identity theft. However, you should read more about it on COPPA.
- Senior Identity Theft: Targeting individuals over 60, as seniors are always seen as an easy target. It is important for seniors to stay aware of evolving methods used by thieves.
- Identity Cloning For Concealment: The thief will impersonate someone else to hide from law enforcement or creditors. Not always they are financially motivated. They make it easier to track with a clear paper trail.
- Synthetic Identity Theft: In these kinds of thefts, the thief creates a fake identity by combining pieces of PII from various sources. For instance, using a stolen social security number with an unrelated birthdate. Tracking such theft is challenging due to activities recorded under a non-existent identity.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
GUARANTEE
How do Identity Thefts happen?

You might be wondering how all of it is done, right? Well, identity theft is a broad term that covers any time anyone swipes your details, like your Social Security number. Then, they use it to set up a new account, purchase, or pull off any other fraudulent activities.
However, thanks to technology and the internet, your personal information is always on the line. If you are not keeping a close eye on your credit files, you might realize that you have been hit until the damage is done.
This is the only reason we suggest our customers access insecure networks with a VPN. You can try using NordVPN because it is very user-friendly. However, Let us check some of the common ways that hackers use to get your data:
Data Breaches
It occurs when someone sneaks into an organization’s consumer data without permission. Commonly swiped information includes full names, Social Security numbers, and credit card details.
Unsecure Browsing
Usually, internet browsing is safe, especially on a well-known website. But if you spill information on an unsecured or hacked website, then you are practically handing your sensitive details to that thief.
Dark Web Marketplace
We know that the dark web is a secret network of websites that are not accessible through regular browsers. People who use the dark web use some kind of special software to hide who they are. It makes it a perfect spot for the hackers.
Hackers might snatch your information and then sell it on the dark web instead of using it themselves. If your details end up on a dark web marketplace, anyone can buy it by putting your identity at risk.
Malware Activity
Malware is like sneaky software that will cause you a lot of problems. Hackers use it to steal your information or spy on what you are doing on your computer. You wouldn’t even know about what is happening around you. Scary, isn’t it?
Credit Card Thefts
One simple way that hackers can mess with you is by swiping your credit card details. If they get hold of that information, then they can buy things without even your information.
This credit card theft can happen through a data breach or someone physically stealing your card, tricky credit card devices, or when your card details hang out on online shopping sites. It means that even your credit card details aren’t safe.
Mail Theft
Even before the internet, some hackers might have gone through your email to find papers with your personal stuff. Anything sent or received by email, like bank and credit card papers, could be taken to get your information.
Phishing And Spam Attacks
There are some hackers out there who use emails, texts, and other online ways to try to grab your important information. They pretend to be from a trusted place and might trick you into opening a wrong file or visiting a fake website where they can lay hands on your information.
WiFi Hacking
When you use your computer or phone on public WiFi like at the airport, a store, or a coffee shop, then a sneaky hacker might “eavesdrop” on your connection. It means that if you type in your passwords, bank details, credit card numbers, social security numbers, or anything important, then a nosy hacker can easily grab it and use it for their own bad plans.
Mobile Phone Theft
Smartphones are like goldmine information for identity thieves, especially if your applications let you log in without a password or fingerprint. If someone swipes and unblocks your phone, then they could see into your apps, emails, texts, notes, and more.
Now, you know that you can be a victim of hackers. This is why we are saying to our readers that taking safety measures is important nowadays. For example, if you use a VPN, all of your identity will be hidden. How can a hacker lay hands on your information if the identity is hidden? So, taking precautionary measures nowadays is really important.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
GUARANTEE
How To Check For Identity Theft?

We know that we can’t completely fight the possibility that our identity might be stolen. So, all that matters is what you should do if you suspect you are the victim of identity theft.
We think that we can take action to spot potential fraud before it starts causing you a problem. Here are some protective measures include monitoring your credit score, keeping an eye on your credit reports, being cautious about sharing personal information, and using tools like VPNs for secure browsing.
Monitor Your Credit Score
We think the main way to check for identity theft is by monitoring your credit score. You should see if there is a sudden drop in your account. It can be a dead giveaway that something wrong is happening around. This is the main reason that we recommend our users to keep a check on their credit score. You can also use apps to see if something goes wrong with your account.
Keep An Eye On Your Credit Reports
You should never ignore your credit reports. Sometimes, there is a glitch in your account and you can’t know if there was an amount taken out or not. However, reports give you details about everything. It means they can tell you if something unusual is going on with your account. You should always look for the tradeline that you don’t recognize or remember opening.
Look At Your Bills
As we told you before, you should look for your bank account and credit card statements to make sure that every transaction made by you is recognizable so, if you are getting a bill, statement, or explanation of benefits from an account that you even didn’t sign up for or a service that you didn’t even get. Then, it probably means it is identity theft.
Read your email
If you think your information was somehow leaked in a data breach, you should receive an email from the company telling you about it. You might also get an email from an app or service that will notify you of a recent login to your account. It means that if it wasn’t you, then it is probably an identity theft.
Some other potential identity thefts are tax returns, which are denied as duplicates. It means that if your credit details are denied despite having an amazing rating or you are not receiving important mail, you will probably become a victim of identity theft. We think recovering from identity theft can take a lot of time.
So, do you know the best way to fight Identity Theft? To prevent it. And we think that the best preventive measure you can take is a VPN. They will encrypt your data and make it impossible for the hackers to access it. If you are unsure about getting the right VPN, try using NordVPN. They are the best in town nowadays.
What Consequences Are Faced By A Person After Identity Theft?

Identity theft can cause big problems for people. If someone steals your personal information to do bad things, you might lose money and property, damage your credit, and face other troubles. There are cases where people get wrongly accused of crimes they didn’t do because of identity theft.
Thieves often use stolen information for fraud. One type, called true name fraud, happens when a hacker takes your personal details and pretends to be you to get credit accounts. True name fraud can mess up your credit score and make it hard to get real loans and credit cards later. So, it is important to act if you think someone got hold of your info without your consent.
But we think the most important thing is to take preventive measures like how you can protect yourself while using public WiFi. You might have to use public wifi due to your remote work or any emergency. And it is a fact that in our lives, no matter what, we have to make use of public Wifi. But we also know that most data breaches occur from there.
So, What do you think is the best way to prevent it all? The best preventive measure is to use a VPN. They are like a savior when it comes to identity theft. Why? Because they are the experts of anonymity. So, if you want to save yourself, then get the best one. If you can’t make a choice, then try using NordVPN. Their amazing features will amaze you. They will help you protect your data from fraud.
What Are Identity Thefts Laws And Penalties?

When you hear the name Identity theft, then you might wonder, “Is identity theft a federal crime?” Yes, identity theft is a federal crime in the U.S. Laws like the Identity Theft and Assumption Deterrence Act and the Identity Theft Penalty Enhancement Act impose fines, restitution, and jail time for perpetrators.
Governments handle identity theft crimes in different ways. In the U.S., there are two main laws that shape how the legal process deals with identity theft: the Identity Theft and Assumption Deterrence Act of 1998 and the Identity Theft Penalty Enhancement Act of 2004.
The Identity Theft and Assumption Deterrence Act makes it illegal to “knowingly transfer or use someone’s identity with the intent to do something against the law federally, or that is a serious crime in any state or local area.”
This law increased the time people can be in prison for certain offenses, both regular and related to terrorism. It also set punishments for aggravated identity theft. Aggravated identity theft is when someone uses another person’s identity to commit serious crimes. The penalties for identity theft can be serious and depend on the situation:
- For some first-time cases where not much harm was done, the thief might get probation but still have to pay fines and compensate for the victim’s losses.
- Most often, the person committing the crime faces felony and misdemeanor charges.
- The thief might have to pay the victim for the money they lost, including wages, legal fees, and maybe even emotional distress.
- In the U.S., identity theft perpetrators often go to jail, with the least time being two years for aggravated identity theft. This time can go up depending on how severe the case is.
Is There Any Identity Theft Insurance?
Identity theft insurance can speed up victims’ slow and expensive recovery process. Usually, it covers only the costs of recovering, not the theft’s direct damages. Depending on the policy, it may cover:
- Lost wages
- Childcare expenses
- Credit monitoring services
- Legal fees
- Copies of credit reports
Identity theft insurance can be added to homeowners or renters insurance or bought separately. Typically, it comes with deductibles ranging from $100 to $500 and benefit limits of $10,000 to $15,000. If damages exceed this limit, the victim must pay the extra amount.
For those seeking alternatives or extra help, identity theft protection services are an option. These services may offer reimbursement for stolen funds, restoration help, and credit monitoring services.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
GUARANTEE
Who Should We Report Identity Theft To?

If you suspect Identity Theft, report it to the Federal Trade Commission at IdentityTheft.gov, file a police report, place fraud alerts on your credit reports, and monitor your accounts closely for any unusual activity.
File An Identity Theft Report
Go to IdentityTheft.gov to officially report identity theft to the Federal Trade Commission. The website offers tools to help you recover, including sample dispute letters for credit reporting agencies. You can send a dispute letter and your identity theft report to any credit bureau, asking them to block fake accounts from your credit report, as your right under the FCRA allows.
File a police report
If you are a victim, report the identity theft to your local police station. Just like the reports to the Federal Trade Commission, send a copy of your police report to the credit bureaus, along with a credit dispute letter pointing out any fake accounts. Ask the bureaus to block these fraudulent accounts on your credit reports.
Fraud alerts
Contact any of the three credit reporting agencies to place a fraud alert on all your credit reports. Tell them you suspect identity theft. Fraud alerts make it tougher for thieves to open new accounts with your info, as creditors must confirm your identity before issuing credit in your name in the future.
How Can We Prevent Identity Theft?

Let’s move on to the last question, which everyone is curious about. You might be wondering which ways we can prevent identity theft. Well, to be real there are many ways that you can use to protect your identity but we will talk about only the best one. And the best one is? Yes, you are right. We are talking about using a VPN.
A Virtual Private Network is the best way that anyone can use to protect their identity. Everyone knows how it works. They are used especially to hide one’s identity. People might take it in the wrong terms, but it is the safest platform for your protection on the internet.
It makes your data encrypted, which can’t be opened without a key. So, how do you think a hacker will be able to crack that lock? With a VPN on, you don’t have to worry about your stuff. All your data will be safe with a VPN.
Well, with many options out there, it might be difficult to pick the right VPN. We knew that, which is why we have got you the top pick of this year. NordVPN. You might have heard it before, but you might be wondering if it is the right choice or not. However, don’t think a lot because it is the best one.
NordVPN, with its amazing features like Double VPN and Onion on the VPN, has doubled its privacy game and stands out in the competition. But if you still want to explore other options, then it is your choice. We are always here to help you through.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
GUARANTEE
The Bottom Line
You now know that Identity Theft is a serious crime that is rising among people nowadays. And the only way to prevent it is to take the right measures. And the right measure is to never let it happen. You should try using a Virtual Private Network, which will hide your identity; even your Internet Service Provider won’t be able to tell if you are there or not.
So, where can you get a better deal than this? We have told you our top choice in VPNs, which is NordVPN. However, exploring other options is never a bad option. But closing your eyes when you have the right one in front of you is also not a wise choice. We hope we have cleared all of your confusion, but if you still have any questions, then feel free to ask us.
Customer Reviews for NordVPN: In-Depth Review, Tests, and Stats

Connection issues with MLB.TV
May, 2 2023

Prompt customer service
May, 6 2023

I would highly recommend
December, 15 2023



