How To Approach Privacy & Data Compliance With New Technology

Do you want to stand online but worried about the ever-increasing cyber threats? Well! Your concern is obvious. As technology continues to advance day by day, privacy and data compliance have become the must-have factors for digital surfers.
It has become necessary that the companies that collect and use user data ensure privacy and data compliance by making it their priority. It will help them build trust among customers, avoid fines, and stay creative.
This detailed article will provide you with a complete overview of privacy and data compliance, reveal why it’s so important in our lives, highlight key challenges, and provide the best possible practices companies can implement to ensure compliance and improve user privacy.
What is Privacy and Data Compliance?

Data compliance is a broader term that covers all relevant data privacy, security, and usage rules. This involves laws like CCPA, GDRP, and industry-specific regulations that command how companies must deal with users, employees, or other relevant information. Compliance shows that an organization is meeting all necessary standards for accurate data management.
Basic Reasons Why Privacy and Compliance
The main causes why privacy and data compliance have become important for companies. The basic reasons are as follows:
- Avoiding huge regulatory fines, lawsuits, and other penalties
- Building user or customer trust and loyalty by respecting their privacy rights
- Holding up to innovation by ensuring that data practices are ethical
- Maintaining functional integrity as non-compliant companies face limitations
Focusing on privacy and data compliance is important from the early design phases when creating new technologies based on collecting and using personal data.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
- Rated 4.5/5 on Google Play with over 825,000 reviews
- Rated 4.7/5 on Apple App Store from 6,600 users
Why are Privacy and Data Compliance Important?

Organizations should prioritize privacy and data compliance in their strategies for many considerable and obvious reasons. Some of them are as follows:
Avoiding Penalties
Controllers globally have charged strict fines and penalties for non-compliant data privacy that have exceeded $1 billion in some serious cases. Staying compliant is compulsory to avoid prevailing threats.
User Trust
Companies instill trust and loyalty among customers by paying heed to their data privacy rights and maintaining transparency around the data collection. Without this trust, users may share less data or take the services of your competitors.
Reputation Protection
Data breaches or unethical data usage harms brand reputations greatly. This also crumbles consumer and public trust over the long term. So, prioritizing “compliance” protects reputations.
Fueling Innovation
When users feel comfortable sharing personal data, companies can gain unique insights to be creative. However, privacy fears hinder this approach and delay competitiveness.
As data utilization increases in society, so does public awareness of the importance of data stewardship.
Companies that ignore this have to pay for damage recovery themselves. Those hoping to use data science must put privacy and data compliance at the core of operations.
Difference between Data Privacy and Data Protection
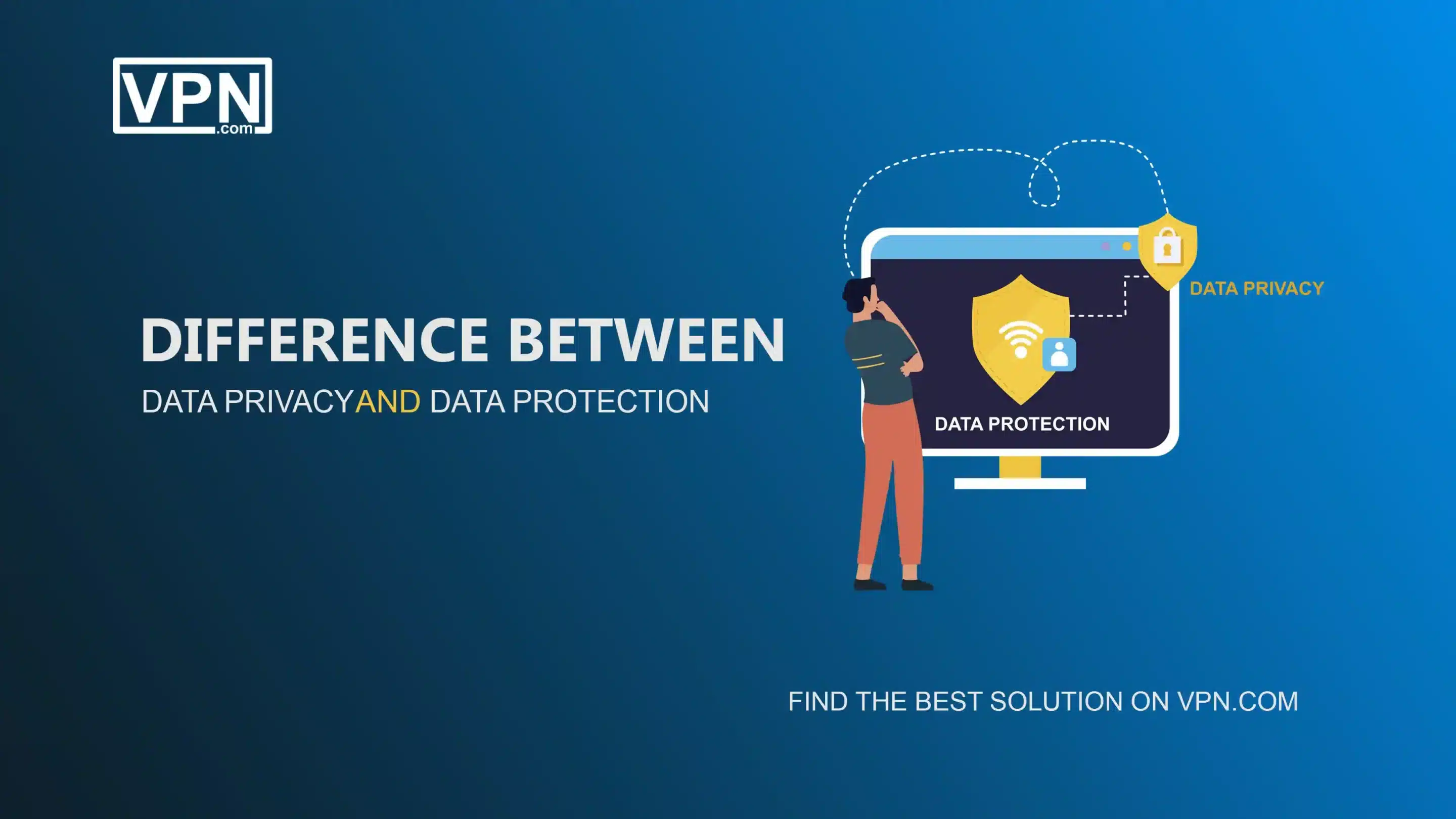
Data privacy means the allowable usage and sharing of user data with transparency commitments made when data is provided by users. Data protection deals more with safeguarding user data by ensuring databases, networks, applications, devices, backups, and other components are secured against unauthorized access or cyber threats.
While different, powerful data privacy and protection are both crucial for compliance, security, and ethics. Some key differences include:
Data Privacy
- It is related to allowable data usage or sharing
- It aligns with user agreements
- It requires transparency for user trust
Data Protection
- It focuses on system or network security
- It prevents unauthorized data access
- It relies on cybersecurity protections
A company may have strong data protections but it still violates user privacy by misusing or over-sharing collected information.
Alternatively, rigid data privacy policies are meaningless if databases are left unsecured. Thus, modern companies must focus mainly on rapidly advancing both privacy & data compliance and data protection.
Surprising Challenges In Data Privacy

Advancing privacy & compliance in the modern, highly networked economy full of cyber threats creates considerable challenges, including:
Complex Data Networks
In the current digital era, data moves instantly across borders and systems in complicated ways. A purchase online can initiate data flows between payment systems, delivery services, review sites, advertisement partners, and more in seconds. Keeping tabs on where data goes and ensuring every stop complies with privacy rules is very hard.
It’s like playing a game of telephone with thousands of players across the globe. New types of security controls and coordination tools are required even to begin untying this privacy mess.
Increasing Data Volumes
As technology advances, companies are collecting more data about customers than ever before. Where people go, what they buy, websites visited, apps used, and more. Managing all this data responsibly is highly difficult, like finding a needle in a haystack.
Even just mapping out and keeping inventories of the tidal wave of data is hugely complex. It’s essential to build very organized systems from the start to handle user data properly as it accumulates so rapidly.
Regulation Gaps
Innovations often race ahead of regulation as governments are confused about adapting old rules or creating new ones reflecting emerging tech effects on consumer privacy. But major gaps remain, especially in emerging tech like AI or ML, facial recognition, and more.
There are too many holes through which precious user data still leaks out despite corporate promises to protect this responsibly. Updates are delayed as lawyers and politicians try to play catch up.
Legal Technology Issues
Many old IT systems are still running companies that lack the basic abilities to properly track data flows or restrict access that modern privacy laws demand. Trying to adopt new capabilities rarely works well and leaving these systems as they are leaves dangerous gaps.
True data compliance and governance become feasible as rules tighten due to costly integration projects or replacing aging platforms.
Talent Shortages
All these rising challenges require specialized skills to navigate properly. However, demand for qualified data privacy or compliance personnel increases while qualified talent remains short. Too few job candidates possess the expertise to architect the systems, controls, and audit procedures that evolving robust data privacy environments require.
Companies can end up trying to maintain their way to compliance, often unsuccessfully without the right guidance. Advanced enrollment and training are vital to fill this talent void.
While necessary for innovation and operations, using data science brings major modern privacy & compliance complications. Organizations hoping to get opportunities while respecting user rights must prioritize solutions for these data privacy challenges.
Best Practices to Ensure Data Privacy

Maintaining strict privacy standards and compliance requires implementing numerous essential best practices. The following are the mentioned practices:
Consent Management
Companies must create very clear and transparent ways for customers to control if their data gets shared or used internally. Too often dense legal jargon hides how data moves. Simple checkboxes upon signup that explain each use in basic terms help. Allowing customers to change data-sharing choices anytime, with no extra steps, builds trust.
Anonymization Tools
Remove tags that identify individuals from databases to assess patterns while protecting privacy through anonymity. Tools can automatically replace real names for code numbers, cluster people into segments, blur specific details, or disorganize parts of the data to hide sources. Proper use separates personal links from broader insights.
Reduced Data Collection
Collect only what’s necessary, not just because you can. More data means more responsibility and a chance of abuse or breaches. Think carefully about why you need data inputs and resist grabbing other points that seem nice but aren’t vital. Every unnecessary bit creates added privacy headaches down the road. Stick to what you clearly must have.
Visibility Tools
Central platforms providing business-wide visibility into data locations, access permissions, data flow between systems, and sharing with outside groups are essential for governance. Imagine driving blindfolded and this is how many companies handle data daily. They simply can’t manage what they can’t see across cloud services, on-site databases, and more. Changing this through indexed mapping and monitoring is essential to achieve data compliance.
Policy Awareness Training
Simply drafting long privacy policies means little if employees don’t understand what they mean day-to-day. Companies must educate all staff on basic rules through regular interactive training. Make sure people recognize everyday data-sharing risks, like emailing spreadsheets with personal details or mishandling paper records.
Training should connect the dots between policies and real-life situations using quizzes, videos, and talks to participate in. Enable everyone to detect potential violations before they happen.
Incident Response Planning
Despite best efforts, breaches happen as cyber threats rise. Having playbooks for quickly detecting and responding to containment helps restrict the damage. Clear plans create order in the middle of chaos so teams don’t lose precious investigative time. Routines for alerting users and regulators and recovering data faster benefit all. Ignoring incident readiness makes suffering obvious.
Global Compliance Reviews
Privacy laws vary across countries and states, rapidly expanding and evolving. What’s compliant in one region may break the rules elsewhere. Companies must regularly audit practices in every location they operate against current local laws to avoid issues. Consider it the regulatory version of high striker trying to stay on top of new and updated data rules across hundreds of authorities. However, systematic compliance reviews are the only way to catch issues before punishments hit.
Encryption Protection
Despite rigorous defenses, data breaches still occur. Encrypting sensitive data elements like Social Security numbers, medical history, bank details, etc., creates another barrier by confusing information. Even if hackers steal volumes of encrypted data, making sense of it becomes much harder buying companies time to reset breached systems.
Think of it as putting private data into a vault, and even if the rest of the building burns down, the valuables survive inside. Want to know how? A robust VPN can do this for you. It encrypts your data effectively and keeps it secure throughout the channel. Visit VPN.com today to get the best VPN that fits your needs.
Third-Party Assessment
Vendors, contractors, or other external partners who are given data must handle it correctly too. Yet security practices vary outside company walls. Reviewing how external entities that receive protected data ensure compliance and close dangerous gaps that regulations ignore. Take partner cyber risks, policies, access controls, and security just like you would audit internal teams to uncover hidden weak links placing private customer data at risk.
Regular Risk Assessment
New technologies, data flows to untested partners, or purchases of startups with immature practices constantly change privacy risks. Companies can’t just assess once. Red team models potential vulnerabilities from new tools, third parties, and emerging cyber threats in the news.
Proactively self-testing for gaps is neglected till real attacks require them. Prioritize areas of maximum uncertainty that audits may miss before incidents strike that could have easily been prevented.
With data utilization growing across industries, focusing intently on “compliance” and data privacy best practices policies is the only way for companies to tap opportunities while respecting user rights in sustainable ways. Those who ignore this responsibility do so at their long-term risk.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
- Rated 4.5/5 on Google Play with over 825,000 reviews
- Rated 4.7/5 on Apple App Store from 6,600 users
Compliance with the GDPR

GDRP stands for General Data Protection Regulations which is a detailed data protection law made by the European Union (EU). The GDRP is more advanced than the 1995 Data Protective Directive, and it helps coordinate data protection laws among EU member states.
The GDRP is applicable to all the businesses within the EU and companies worldwide that use the personal data of the EU natives. Compliance with GDRP is essential as it applies to any of the following conditions:
- The business is based in the EU and utilizes the personal data of EU citizens.
- The business deals in products or services to EU citizens, even if it’s not based in the EU.
- The business analyzes the behavior of EU citizens, such as tracking their online activities.
The GDPR is based on seven basic principles :
- Lawfulness, fairness, and transparency
- Accuracy
- Integrity and confidentiality
- Accountability
- Data minimization
- Purpose limitation
- Storage limitation
Businesses have many responsibilities when handling EU citizen data under GDPR. They need to follow certain rules. Here are some key points:
- They must have a valid reason for collecting, storing, processing, or selling data.
- If they use consent as the reason, it must be freely given and clear.
- People have the right to request access to their data. Businesses must honor these requests.
- If there’s a data breach, the company should inform the relevant authority within 72 hours.
- Businesses need an appointed data protection officer (DPO).
- In some cases, they must do data protection impact assessments (DPIAs) and records of processing activities (RoPAs).
Each EU country has its data protection authority (DPA). DPAs investigate complaints and make sure businesses follow GDPR rules. Each DPA has its guidance, which can make compliance tricky across the whole EU.
Businesses need to comply with GDPR. If they don’t, they can face big fines; over 4% of their yearly global revenue or €20 million, whichever is higher. To help with data compliance, many businesses use GDPR compliance automation systems. This lets them focus on their main work while still following the rules.
Compliance with CCPA

The CCPA and CPRA have a big impact on businesses in California. This is especially true for businesses that collect and use the personal information of California residents. Businesses need to follow the rules of the CCPA to achieve data compliance. If they don’t, they can face big penalties.
Here are some of the key things businesses must do under the CCPA:
- Respect consumer rights: Businesses must listen to requests from consumers. This includes the right to say no to having their data sold or shared, the right to see and delete their data, and other requests.
- Limit transfers of personal information: If a user asks, businesses must not sell or share their personal information with outside parties.
- Limit use of sensitive personal information: Sensitive information like Social Security numbers and health data can only be used for the main reason of the customer’s transaction.
- Minimize data: Businesses should only collect and keep the data they need.
- Do risk assessments: If collecting or using personal data is high-risk, businesses must do assessments to find and reduce potential risks.
- Have contracts: Before sharing, selling, or giving personal data to other parties, businesses must have contracts in place to protect the data.
CCPA compliance software can help businesses avoid big penalties if they don’t follow the rules. The California Attorney General and the California Privacy Protection Agency (CPPA) enforce the CCPA. The penalties for not following the CCPA can be:
- $2,500 for each violation
- $7,500 for each violation done on purpose
- $7,500 for each violation involving the personal data of a minor (someone under 18)
Data Protection Trends

While maintaining rigorous privacy standards is imperative, rapidly advancing data protection defenses is equally vital to truly secure sensitive customer data from exponentially growing cyber threats. Some top modern data protection trends include:
Automation Use Growing
There’s simply too much going on for overwhelmed security teams to keep up with manual processes. Automating boring tasks like patching software, encrypting data, backing up files, and monitoring access patterns uses AI efficiencies so defenders can focus on critical thinking. Just like self-checkout expands cashiers’ attention, cyber automation expands human abilities to outsmart growing threats.
Zero Trust Adoption Rising
The old castle and moat approach to security is dying as attacks persist. Zero trust flips security to distrust everyone equally – staff, contractors, and partners alike. Every login attempt gets challenged, and access is granted temporarily and on minimum need. Data stays locked down fearing breaches, only moving within isolated channels. While complex to enable, zero trust better reflects the ugly reality that persistent threats are the norm.
Proactive Cyber AI
Basic rules fail against unpredictable attack patterns. New cyber AI analyzes deep data points through machine learning – identifying behaviors that give rise to 99% of breaches missed by humans. By acting on mathematically certain irregularities rather than guesses, precision skyrockets allowing understaffed teams to neutralize threats early before damages occur.
Cloud-Native Security Tools
Traditional network security gear creates cloud-centric environments leading to gaps. New breeds of tools made for elastic clouds and containers uniquely trace resources, workloads, and data flows. Cloud-native security finally speaks to applications’ language matching velocity and flexibility demands native clouds unlocked. It underpins encrypted, identity-first zero trust models.
Unified Controls
Instead of segmented security policies varying between devices, networks, clouds, and apps, unified controls centralize services. One dashboard sets rules covering the messy digital estate most companies now operate to boost flexibility. Universal authentication factors that users apply once on any system, such as encrypted tunnels, move data safely between touchpoints. Converged platforms close multi-technology loopholes.
Embedded Data Protection
Shift to integrate security deeply and earlier when creating software, infrastructure, and data science tools rather than leave it as an afterthought.
As threats increase, relying on yesterday’s security strategies will automatically fail. Companies getting the most value from data science make innovation by coupling it with modern, rapidly evolving cybersecurity and data protection best practices to prevent devastating breaches.
FAQs
What are the consequences of lacking data privacy & compliance?
Major regulatory fines, lawsuits, damaged trust or reputation, restrictions on data practices, and lost competitive advantages from an inability to use data science ethics are some major consequences.
What steps can companies take to start enhancing privacy & compliance practices?
Conduct in-depth data mapping, institute data classification guidelines aligned with regulations, implement logging or monitoring, train personnel on policies, and create cloud-first data protection rules.
How can companies maintain privacy & compliance using AI tools?
Extensive testing for biases and fairness issues enables clarity features to increase transparency, carefully craft accurate training datasets, monitor for accuracy flow, and institute human monitoring processes over high-risk AI.
Why does data privacy matter more than ever before?
The exponential growth in data generation, business reliance on data science, increasing connectivity through digital transformation, and advancement of powerful analytics increase potential misuse and harms that increase the significance of responsible privacy protections.
What are the most important privacy & data compliance regulations companies need?
Globally – GDPR, CCPA, LGPD. Industry-specific healthcare, telecommunications, and financial services rules also apply to relevant authorities on top of broader regulations. Regular reviews are needed to account for frequent changes.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
- Rated 4.5/5 on Google Play with over 825,000 reviews
- Rated 4.7/5 on Apple App Store from 6,600 users
The Bottom Lines
To sum up, we can say advancing privacy & data compliance and protection has progressed far beyond just a best practice. It has become a necessity for any organization to utilize the power of data science in the modern economy.
Companies unwilling to place privacy at the center of operations face approaching threats from consumers, regulators, legislators, and competitors leading the way in ethical, secure data usage.
Prioritizing privacy & data compliance today future proves organizations against rapidly evolving risks as threats and data-sharing controversies escalate globally across sectors.
Matching any innovations in analytics and emerging technologies with equal intensity on privacy & compliance is the only way forward for sustainable businesses. So, the time for action is now! Visit VPN.com and get a robust VPN to protect your sensitive data from cyber crooks.
Customer Reviews for NordVPN: In-Depth Review, Tests, and Stats

Connection issues with MLB.TV
May, 2 2023

Prompt customer service
May, 6 2023

I would highly recommend
December, 15 2023



