iPhone Password Data Leak
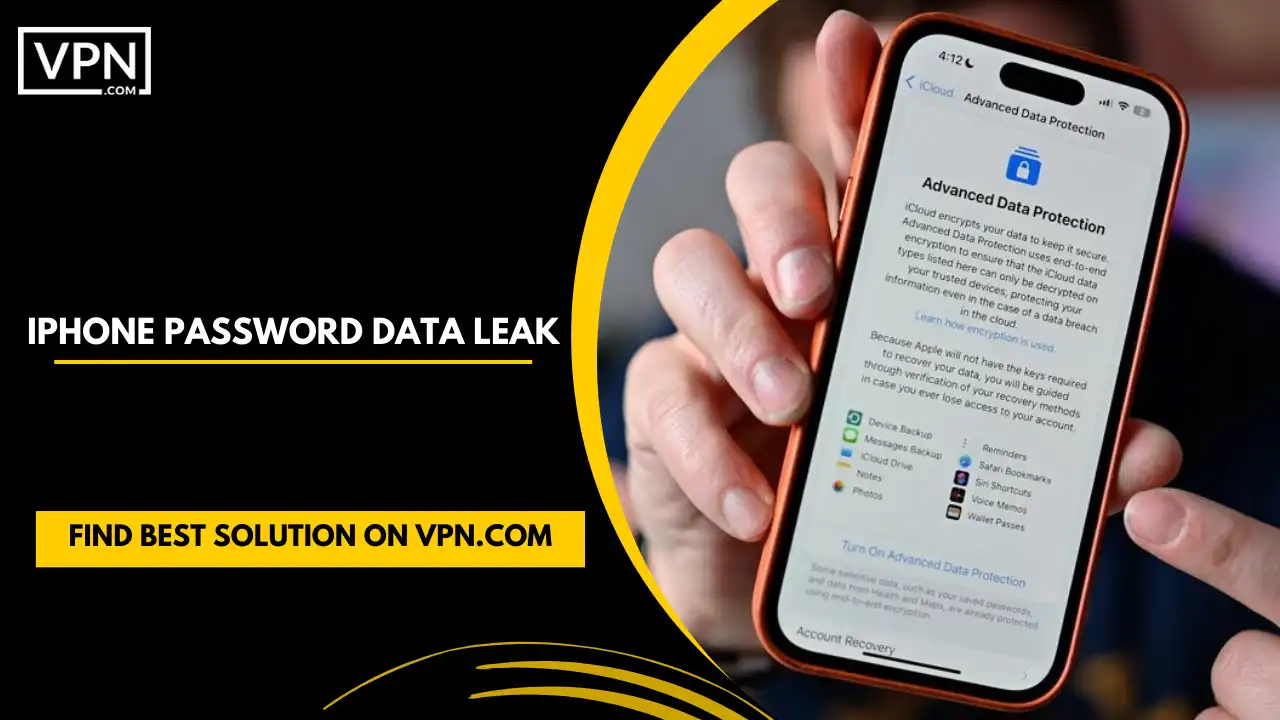
The iPhone password data leak tragedy recently set social media on fire as a major security breach. Privacy is a concerning issue and this incident has underlined the dire need for a more protected online activity. This issue increases potential concerns about how easily our data can be compromised in the cyber world, making it essential to discuss this topic further.
This article will thoroughly explain the incident, from the data source to the repercussions faced by Apple customers and the solutions recommended.
Moreover, other lessons derived from this incident such as cybersecurity awareness and password protocols will also be elaborated in this ultimate lead. So, if you are an iPhone holder and want to protect your confidential details, read this article till the end!
What is a Data Leak?
A data leak occurs when your personal details, like photos or passwords, are exposed to the public eye. It’s significant to know that a data leak is not always a data breach. Data breaches are caused by cyberattacks while data leaks are allied with harmful links you click without expecting anything dangerous.
A data leak is a serious data security issue because once your private data goes into the wrong hands, cyberpunks can use it to execute counterfeit activities, identity theft, or financial fraud.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
GUARANTEE
What Makes iPhone Password Data Leaks Happen?

Investigations have shown that the jeopardized software and hardware played an important role in happening of the leak. By keeping the technological development in view, these weaknesses have subjected critical defects in the previous infrastructure that need to be discussed without further delay.
These incident has increased questions related to the future of data security and privacy for users highlighting the need for powerful security measures.
As we deal with the serious consequences of this shocking breach, it’s important to analyze and reassess the strategy we use to protect our confidential information and cyber profiles.
Making a strong infrastructure that effectively copes with the oscillating risks in today’s interlinked world is the foundation for protecting data security and recovering our digital privacy.
Why Should I Be Concerned About Data Leaks?
Data leaks, like the iPhone Password Data Leak, can seriously endanger your privacy and security. Personal details that are leaked can either be misused for identity theft or malicious activities.
Commercial secrets that are leaked, as demonstrated in cases like the iPhone Password Data Leak, can provide competitors an edge in the market. Confidential details that are leaked can cause financial damage or other damages to your business.
Background on the iPhone Password Data Leak

The password data leak can be linked back to a series of events that ultimately give rise to an immense breach in digital security. At first, an unsuspicious victim falls victim to a precisely crafted phishing email, which gives intruders entry into their system.
With time, the cyberpunks can penetrate deeper into the victim’s network, quietly collecting private information, including login details for different platforms. Eventually, the stolen passwords were collected and shared with a vast network of cybercriminals.
The participants involved in this data leak mainly include highly trained hackers who are experts in implementing manipulative schemes, as well as their associates, who work with them to make these breaches happen on a global level.
As the world is becoming interlinked through the Internet day by day, protecting private data become more important than needed before. Cybersecurity practices should be examined regularly, and modified to cope with the ever-changing threat world and to avoid similar events from happening from now on.
Impact Of The iPhone Password Data Leak

The past data leak incident has undoubtedly increased significant concerns regarding user privacy and security, probably leaving them susceptible to fraud, identity theft, and other vicious activities.
As users highly depend on media technologies and devices to save private information, the possible outcomes of such breaches become even more disturbing. In addition to the imminent threat to user security, this incident unavoidably put Apple’s lofty reputation in doubt as being steadfast in terms of user privacy and data protection.
As a result, the company’s authenticity and dedication to protecting the personal details of its users may be challenged, leading to undermined trust and customer loyalty.
Furthermore, this miserable turn of events may impose serious financial consequences on Apple and its investors, both directly in terms of lawsuits, penalties, and user repayments and indirectly via considerable loss of market share, reduced brand reputation, and lower profit generation.
To sum up, we can say that the ramifications of the data leaks are versatile, impacting users, Apple’s reputation in the market, and financial performance, highlighting the dire need for powerful data security and preventive measures in the constantly changing digital world.
How to View Which Password and Data have been Leaked?
Here are some steps that may help you to find out which of your personal information is revealed online:
- Click “Settings”.
- Now tap on “Passwords” mentioned in the menu.
- Navigate to the “Security recommendation” page.
- Activate the switch button displayed next to “Detect compromised passwords.”
Here you will get different types of recommendations. High-value recommendations will take you through the passwords that might be most vulnerable to breach and other recommendations will show you reused and weak passwords that you should alter to improve your online profile security.
How Can I Protect Myself from iPhone Password Data Leak?
There are a lot of ways to protect your confidential data from the malicious activities of bad players. Some of them are discussed here:
Use Password Managers Carefully
Password managers are a preferable option for users trying to protect their private data effectively, without putting any effort into memorizing innumerable unique passwords. Many famous browsers, such as Safari, Firefox, and Chrome, now provide password management features.
There are also extraneous password management solutions, like LastPass and 1Password. They work by saving a single master password, protected by robust encryption algorithms and techniques like hacking.
While these practices make use of powerful cybersecurity techniques to guarantee the protection of your data, it’s essential to keep in mind that all third-party suppliers have some risks associated with them.
For instance, LastPass was attacked by hackers in a data breach in 2015. Although master passwords were preserved safely, other sensitive details were jeopardized, such as:
- Password reminders
- Authentication hashes
- User email addresses
- Server-per-user salts
Delete Inactive Accounts
Accounts that you don’t use anymore are an easy mark hackers as their security layer is most probably weaker than that of your widely used services.
Monitoring all of your accounts and deleting or deactivating any idle ones is the best way to lower your vulnerabilities and maintain vigilance on your attack surface.
Create Complex and Strong Passwords
Easy passwords make your account vulnerable to brute-force attacks, a common credential-detecting method utilized by hackers to gain unauthorized access to sensitive data. This risk was notably highlighted in incidents like the iPhone Password Data Leak. If your password is revealed in a data leak, all accounts that can be logged in using the same password are now susceptible to attack too.
Setting new passwords for all accounts requires time, but a hacker, especially in situations similar to the iPhone Password Data Leak, who is after your credit card details, will demand money. So, now you have to decide what’s better to do; creating new passwords or paying a huge sum of money to the hacker to restore your account.
Change Your Password Regularly
Several apps and services, particularly in the context of incidents like the iPhone Password Data Leak, want you to renew your password regularly to enhance your account security. Those who don’t update their passwords must know that it’s a best practice to do so.
Regular password updates, a lesson underscored by the iPhone Password Data Leak, limit the ways for hackers to breach private information and work as a long-term reminder of what accounts you are currently using.
Keep Your Software Up to Date
Zero-day vulnerabilities, like those exposed in incidents such as the iPhone Password Data Leak, arise daily and technologists need to work immediately on software patches before hackers misuse them. These security updates are only beneficial if the users are also interested in downloading them.
However, updates, as evidenced by scenarios like the iPhone Password Data Leak, are inconvenient to some extent too. They allow cybercriminals to get access to your data which is even worse.
Set Up Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA)
Strict rules for third-party data breaches, especially after incidents like the iPhone Password Data Leak, represent that organizations (most prominently SaaS services and products) are paying heed to improve account security. Most reliable online services demand or at least strongly suggest creating 2FA or MFA to obtain access to the account.
These techniques, emphasized in the wake of the iPhone Password Data Leak, provide extra protection against account breaches by promoting extra authentication, such as security codes, one-time passwords (OTPs), and biometrics.
Response to iPhone Password Data Leak

Apple’s valid response to the data leak has been widely recognized as evidence of the company’s dedication to protecting user data and privacy. Discussing customers’ concerns clearly and without any delay, Apple was able to restore the trust and confidence of its investors, despite of recent tragedy caused by the leak.
The media also praised the company’s quick response to overcome the consequences of the iPhone Password Data Leak, further strengthening the impression that Apple is still a reputable and responsible player in an ever-evolving digital landscape.
Consequently, this prominent event, notably the iPhone Password Data Leak, has triggered a prolonged conversation around data security and privacy, highlighting the need for persistent alertness and novelty in protecting digital assets, both for individuals and businesses.
The Apple data leak acts as an important reminder that, despite the best efforts, breaches can happen anyway. So, it’s an organization’s responsibility and potential to quickly address such incidents that leave a long-term impression.
Will Apple Compensate Users Affected by the Data Leak?

Apple has always been known for its powerful dedication to protecting user privacy and security. Although data leaks and other security issues don’t occur frequently, it’s essential to know how Apple answers such concerns and what measures this digital powerhouse takes to pay compensation in case of any tragedy.
Apple’s policies, particularly highlighted in the iPhone Password Data Leak, revolve around clarity to make sure that affected consumers are informed on time about any powerful legitimate or regulatory actions that may become a part of compensation. Compensation can alter based on the nature and intensity of the breach, but Apple is careful in implementing measures to adjust the situation and help prevent any mishap in the future.
To protect themselves from incidents like the iPhone Password Data Leak, users should obey best practices to safeguard their personal and financial data. This involves frequently checking bank accounts and credit reports to detect any fraud or illegal activity. Being vigilant and staying up to date about prevailing risks can greatly reduce the effect of any data leak and ensure peace of mind in the present digital landscape.
Lessons Learned And Recommendations
The iPhone password data leak event acts as an essential reminder of the dire need for powerful data security and privacy measures. Taking valuable lessons from this miserable situation, it becomes significant for organizations to completely assess and establish their cyber force structure by implementing encryption, two-factor authentication, and complex passwords that are hard to crack.
People, too, need to be careful in protecting their private data by using the strongest passwords and renewing them with time, especially in the wake of the iPhone Password Data Leak. Attaining a vigilant approach to data safety can considerably lower the risk of such breaches in the future.
Moreover, the iPhone Password Data Leak event highlights the broader consequences for the tech industry, forcing it to review its security techniques and adopt a clearer strategy for data management. By responding to these challenges on time, the company will not only maintain greater customer trust but also promote a more stable digital environment for all.

Get Started w/ NordVPN Today
- Top-rated VPN for OS unknown
- Ultra-fast speed in US in 2024
- Save 69% off with VPN.com Discount
- Plans starting at $2.99/month
GUARANTEE
Conclusion
The iPhone password data leak incident acts as a harsh reminder of the robust need for more extensive implications on data privacy and security in the modern age. This event sheds light on the new challenges faced by the leading technology firms as well as the individuals as they work to ensure that personal and collective data is protected in an ever-evolving interlined world.
Ruminating the greater importance of the iPhone Password Data Leak incident, it requires us to be more alert and enthusiastic in protecting our cyber profiles. In this era of continuously evolving threats to online security, highlighted by the iPhone Password Data Leak, it’s significant for governments, organizations, and daily users to act in collaboration to improve privacy controls and stay one step ahead of nasty cyber crooks.
As the digital world is getting more and more interconnected day by day, take this incident as a warning shot for the importance of enhancing data security in our digital lives.
Customer Reviews for NordVPN: In-Depth Review, Tests, and Stats

Connection issues with MLB.TV
May, 2 2023

Prompt customer service
May, 6 2023

I would highly recommend
December, 15 2023



